
ConsentFix: A New way to Phish for Tokens
A look at a new phishing campaign, ConsentFix which utilises click-fix style techniques to steal auth tokens.
15 articles on cybersecurity research, malware analysis, and threat hunting

A look at a new phishing campaign, ConsentFix which utilises click-fix style techniques to steal auth tokens.

A walkthrough of different Token Theft Scenarios with Detections
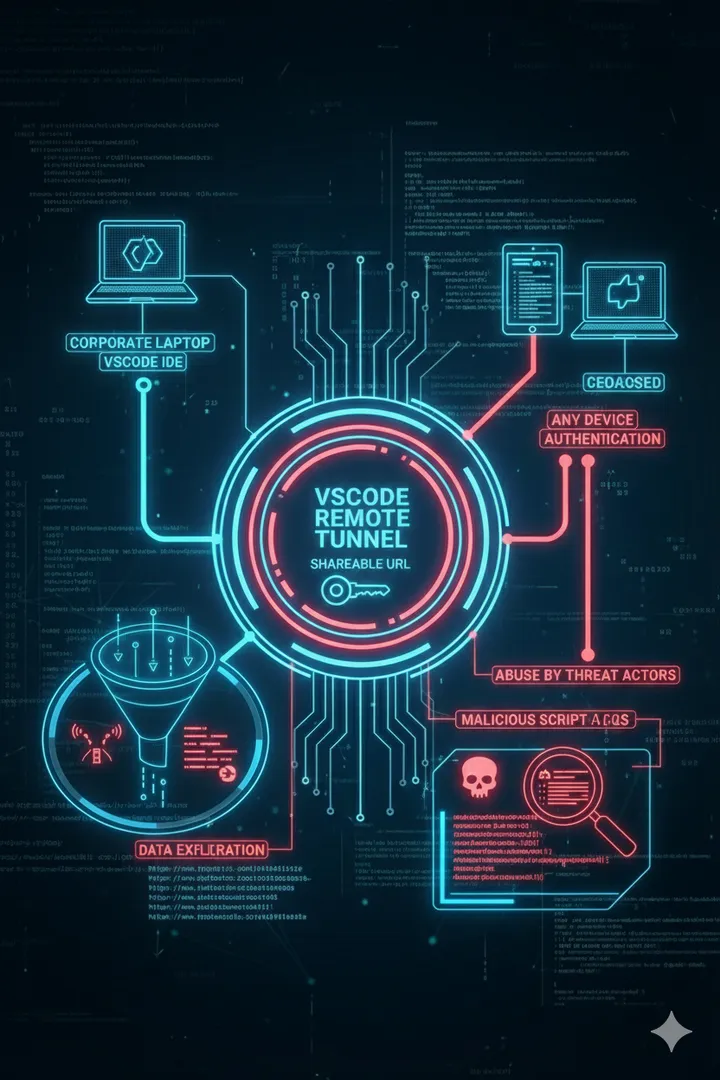
Detecting abuse of VSCode Remote Tunnels for C2 and persistence by threat actors

How threat actors abuse Microsoft Dev Tunnels for C2 communication and detection strategies
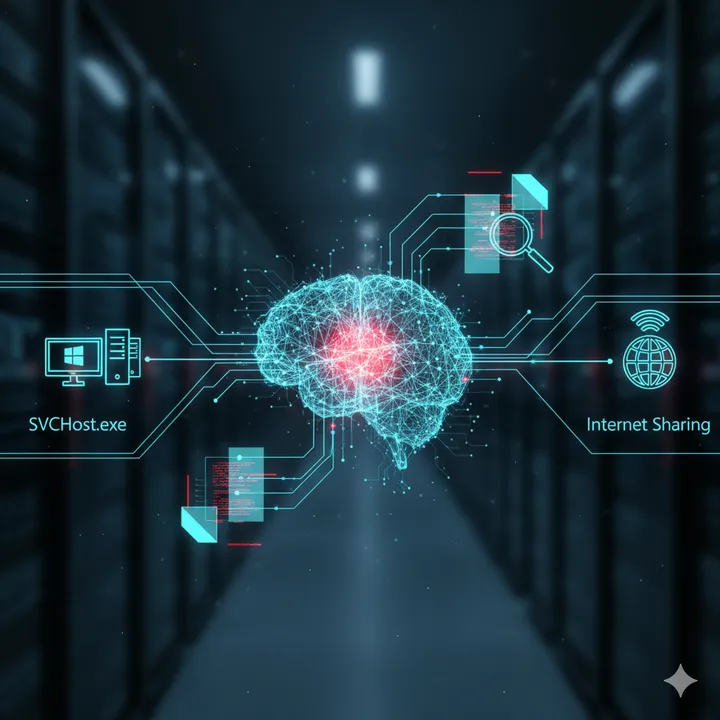
Investigating suspicious svchost.exe behavior and Internet Connection Sharing during malware triage
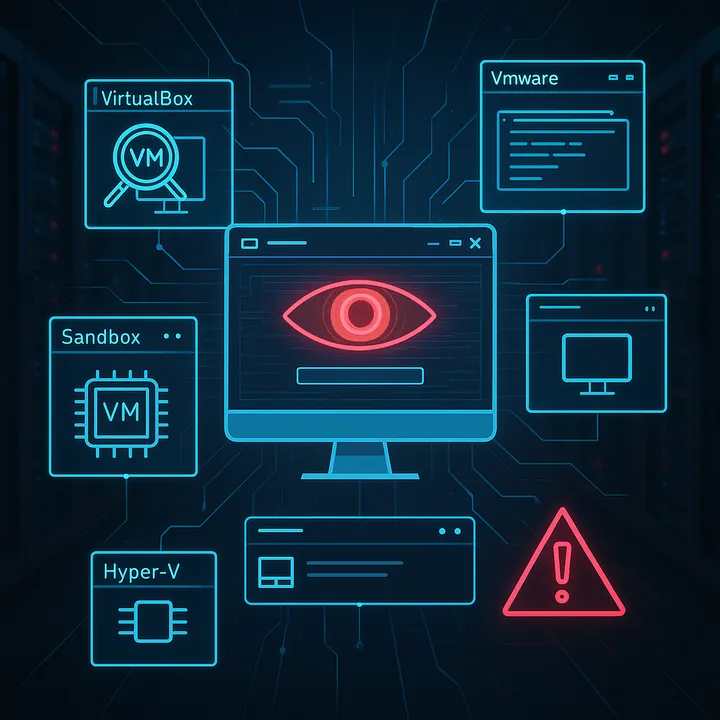
Analysis of phishing kits that detect and evade virtual machine environments

A practical guide to implementing threat hunting in a SOC environment and moving beyond reactive detection
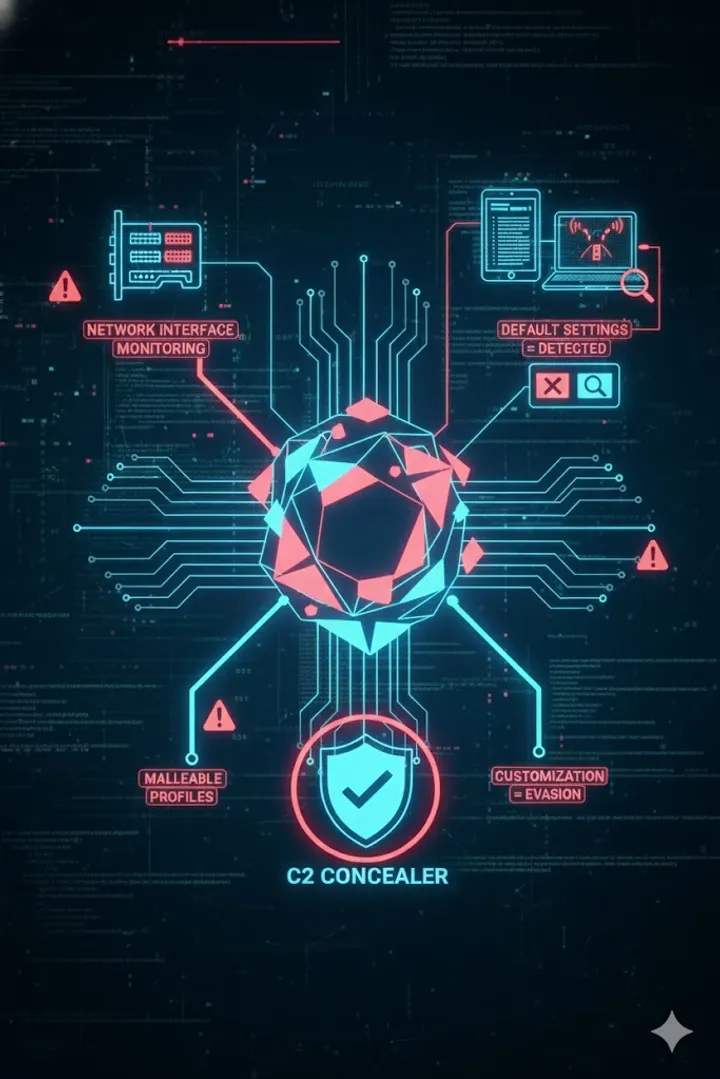
Using Malleable C2 profiles and C2 Concealer to bypass network-based detection of Cobalt Strike beacons

Complete guide to installing and configuring Elastic SIEM with EDR capabilities
Using Volatility 3 for memory forensics to analyze malware-infected systems
Step-by-step analysis of a multi-stage fileless malware campaign delivering Cobalt Strike beacon

Configure Filebeat to ship Zeek network logs to ELK Stack for home network monitoring

Build a home network monitoring lab using Zeek IDS and ELK Stack for traffic analysis
Understanding and exploiting Local File Inclusion vulnerabilities through practical pentesting
Analyzing malicious Office documents using OLE Tools and CyberChef for static analysis